The original syslog protocol was defined in RFC 3164. However, since it was never officially standardized, a new standard, RFC 5424, was introduced to clarify and extend the specification. CLIP transmits messages exclusively in the RFC 5424 format. Configuration is done using the parameters facility: 1 (user-level messages) and severity: 6 (informational).
Field names and values are represented as "field"="value" pairs, separated by spaces.
The different value types are formatted and transmitted in ASCII as follows:
c-strings remain unchanged
Numbers are represented as strings of digits (0–9)
x-strings are represented as strings of hexadecimal characters (0–9, A–F)
Keywords are translated into their corresponding descriptive meanings
Currently, CLIP processes security-relevant BS2000 events and messages from the following sources and forwards them in RFC 5424-compliant syslog format to an external server, such as an rSyslog server:
SAT (Security Audit Trail)
Field names and values are documented in the official SECOS manual.Note
HEADER and TRAILER record of a SAT file are written directly to the file. Therefore, the corresponding SAT events ZBG and ZND are not transferred to CLIP and cannot be logged there.
ACCOUNTING (Accounting records)
Details are provided in the following section.
rSyslog is a widely used open-source tool for forwarding log messages based on the syslog protocol.
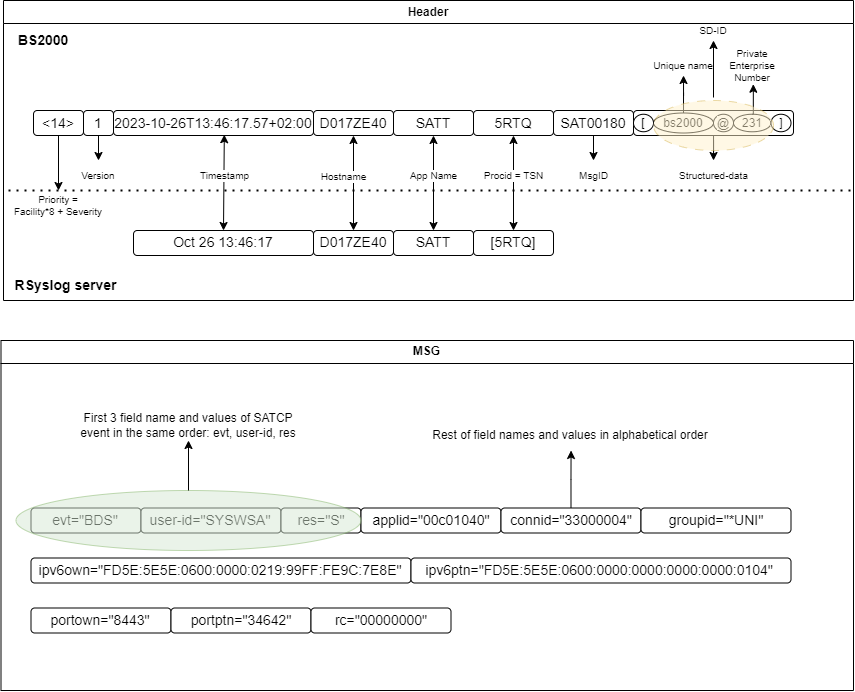
The message format used by CLIP is described below. The structure of the header fields is defined in RFC 5424.
Example of a syslog message transmitted by CLIP over the network interface:
<14>1 2023-10-26T13:46:17.57+02:00 D017ZE40 SATT 5RTQ SAT00180 [bs2000@231] evt="BDS" user-id="SYSWSA" res="S" applid="00c01040" connid="33000004" groupid="*UNI" ipv6own="FD5E:5E5E:0600:0000:0219:99FF:FE9C:7E8E" ipv6ptn="FD5E:5E5E:0600:0000:0000:0000:0000:0104" portown="8443" portptn="34642" rc="00000000"
Example of how this message is displayed on a Linux rSyslog server:
Oct 26 13:46:17 D017ZE40 SATT[5RTQ] evt="BDS" user-id="SYSWSA" res="S" applid="00c01040" connid="33000004" groupid="*UNI" ipv6own="FD5E:5E5E:0600:0000:0219:99FF:FE9C:7E8E" ipv6ptn="FD5E:5E5E:0600:0000:0000:0000:0000:0104" portown="8443" portptn="34642" rc="00000000"
The structure of the message is illustrated in the figures that follow.