Data access control refers to the rules regulating the access of subjects to the objects of a DP system, as well as to the methods used to ensure that these rules are actually observed.
BS2000 OSD/BC
BS2000 OSD/BC provides access protection mechanisms for objects which can be administered by DMS (file management system). DMS provides object management for files which are DMS objects.
The following protection mechanisms exist for files:
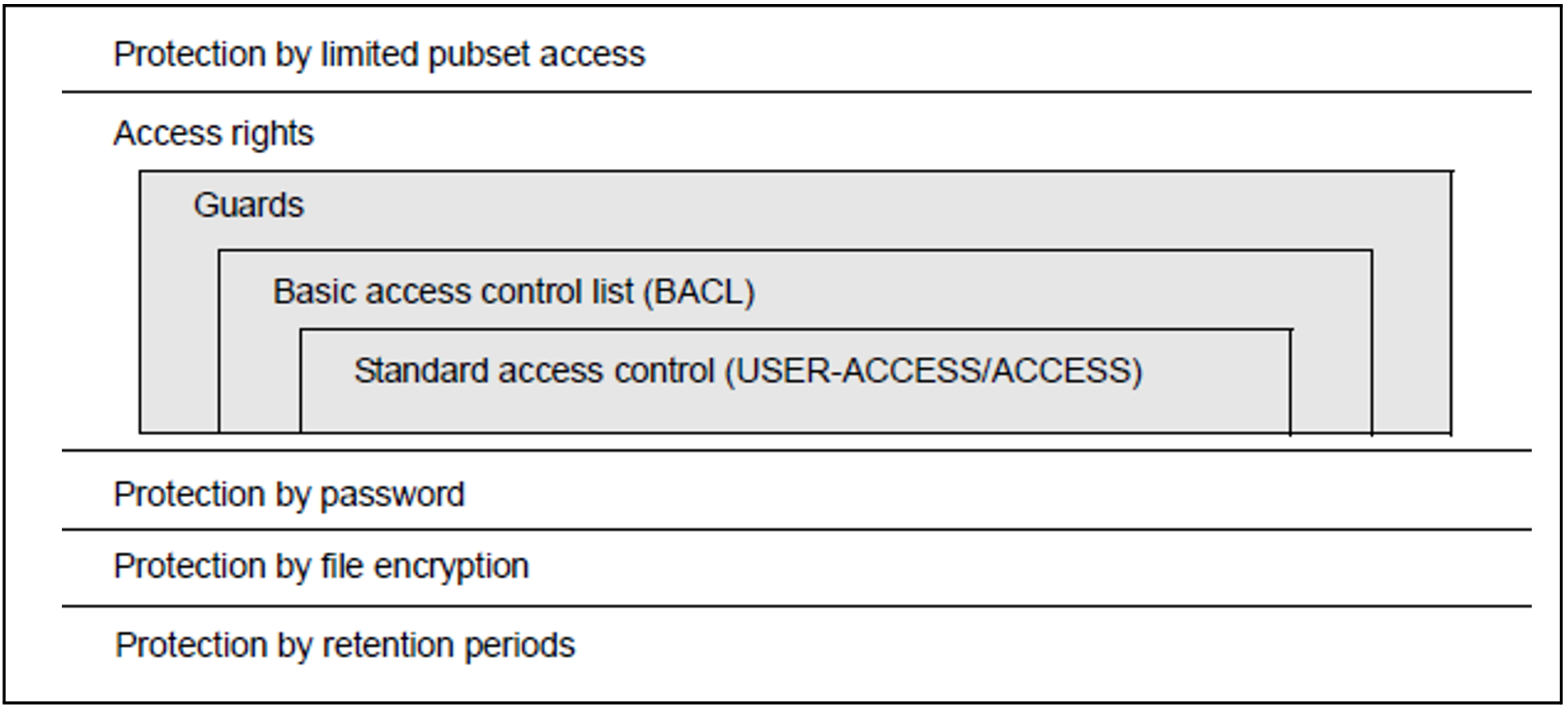
Limited pubset access
By distributing user IDs to different pubsets it is possible to protect against unauthorized access to objects such as files on other pubsets (see also chapter "BS2000 user management" and chapter "Pubset management").Standard Access Control (USER-ACCESS/ACCESS)
The standard access control mechanisms (with the ACCESS and USER-ACCESS operands of the CREATE-FILE and MODIFY-FILE-ATTRIBUTES commands) allow users to define access rights for themselves and others (see "Standard access control (ACCESS/USER-ACCESS)").Basic Access Control List (BACL)
The BACL access protection mechanism allows users to define access rights to files for complex sets of subjects (see "Basic Access Control List (BACL)"). The read, write and execute (exec) acess privileges can be assigned separately for every one of the user classes owner, group and others.Password
It is possible for the user to define passwords (read, write and execute passwords) for every one of his files. The corresponding password must be entered before password-protected files can be processed. Passwords may be encrypted if required (see "Passwords and retention periods").File encryption
The user can convert a file into an encrypted format, specifying a crypto password (like a “normal” password, but 8 characters long). Access to the file contents is then possible only when the correct crypto password has been specified (see "File encryption").
Encrypted files do not have a read or execute password, but can otherwise be combined with all the other access control mechanisms.Retention period
A user can assign his file a retention period in which the file may not be changed (see "Passwords and retention periods").
Security with Cryptography
The BS2000 subsystem CRYPT offers cryptographic functions for BS2000 users7. It uses standardized open interfaces for encryption and decryption of data, see the “CRYPT” manual [9]. CRYPT does not require special hardware.
Extended data access control with SECOS
The software product SECOS (GUARDS component) is a convenient, flexible administrative tool with which it is possible to define and evaluate access conditions for objects such as files, libraries, library elements or other objects of various object management systems. The access protection for the named objects is performed by so-called guards in which the access conditions are stored. Access conditions are queried by object management systems (DMS, LMS, JVS, HSMS, SRPM, etc.). The object management system then grants or refuses access depending on the result of the evaluation.
Using protection mechanisms
The following table shows, which object types can be protected by which protection mechanism:
Protection mechanisms Object | Limited pubset access | ACCESS | BACL | PASSWORD | File | Retention | GUARDS | |
File1 | public | + 2 | + | + | + | + | + | + |
temporary | - 3 | - | - | - | + | - | - | |
private | - | + | + | + | - | + | - | |
tape | - | + | - | + | - | + | - | |
File generation | Index public, FGen public | - | + | + | + | + | + | + |
Index public, FGen tape | - | + | + | + | - | + | + | |
Index private, FGen private | - | + | + | + | - | + | - | |
permanent | + | + | + | + | - | + | + | |
Job variable | temporary | - | - | - | - | - | - | - |
Library element4 | - | - | + | - | - | - | + | |
FITC port | - | - | - | - | - | - | + | |
Storage classes | - | - | - | - | - | - | + | |
HSMS management classes | - | - | - | - | - | - | + | |
Table 32: Protection mechanisms for objects
1 If the file is a library, see "Special cases when accessing libraries"
2 + means: Protection mechanism can be used
3 - means: Protection mechanism cannot be used
4 see "Special cases when accessing libraries"
As the table shows, some objects can be protected with multiple protection mechanisms. Of the ACCESS/USER-ACCESS, BACL and GUARDS protection mechanisms, only one can be in effect for an object at any time (see below). All other protection mechanisms are also valid.
Hierarchy of file access protection mechanisms
When the ACCESS/USER-ACCESS, BACL and GUARDS protection mechanisms are applied to the same object at the same time, contradictory situations can arise. The following hierarchy is used to prevent this from happening:
If protection with a guard is specified for an object, then only the access conditions specified for the guards apply. Any BACL conditions defined for the object as well as the protection attributes ACCESS/USER-ACCESS are ignored.
If no protection with a guard is specified for an object, but BACL is, then the protection settings specified in the BACL are valid. The protection attributes ACCESS and USER-ACCESS are ignored.
If the object is not protected with guards or BACL then the ACCESS and USER-ACCESS protection attributes are used as the protection mechanism.
Limited pubset access, password protection, file encryption and the retention period apply additionally in all cases.
Figure 19: Protection mechanisms for files on a pubset
Every file and every job variable can be protected using one or more protection mechanisms. The access rights have the following priorities:
GUARDS
BACL
Standard access control
One and only one of the three protection mechanisms is used for checking access authorization. This is namely the one that is the highest in the hierarchy and is active.
Special cases when accessing libraries
PLAM library files can be protected as a whole like a file. Library elements can be protected using the LMS statement MODIFY-ELEMENT-PROTECTION regardless of the library file protection.
You must therefore note the following when accessing libraries and library elements:
Access to individual library elements is controlled by the protection mechanism specified with MODIFY-ELEMENT-PROTECTION. Regardless of the element protection, this type of access is only possible, however, when permitted to read the entire library file.
When accessing an entire library (with ARCHIVE, with File Transfer or with the DMS command COPY-FILE), the following applies:
If the library is not protected by a BACL or guards, then you can access it just like any other file.
The access rules in the following table apply when accessing a library that is protected by a BACL or a guard:
Library contains at least one element that is protected by a BACL or a guard
Library contains no elements that are protected by a BACL or a guard
Access
by
Owner
* 1
*
Co-owner
*
*
Others
Access prohibited
*
Table 33: Access rules when accessing libraries
1 * means: Access depends on access rules of the library as a whole