The lock/key code concept allows you to determine, for example, that only users or client programs with a particular type of authorization can use particular services of the UTM application UTM. You can also specify that signing on under a user ID is only possible via certain LTERM partners (access points) or that certain services can only be started via specific LTERM partners. It is thus possible to restrict the authorization of a user to start a particular service to the use of a specific, particularly secure terminal or client system.
The objects to be protected (e.g. LTERM partners, transaction codes assigned to services) are provided with a lock code, which takes the form of a logical number lock. Key codes are defined for user IDs and LTERM partners. If a key code matches the lock code of a protected object, access is granted to this object.
A user ID or an LTERM partner generally has access to a number of services, and therefore has several key codes. The individual key codes are combined to form key sets.
The lock/key code concept results in the following effects:
A terminal user or a client program can sign on only if the specified user ID is assigned a key code that matches the lock code of the relevant LTERM partner.
A terminal user or a client program can call a particular service only if the key sets of both the respective user ID and the LTERM partner contain a key code that matches the lock code of the transaction code.
The diagram on the next page shows an example of how to use the lock/key code concept.
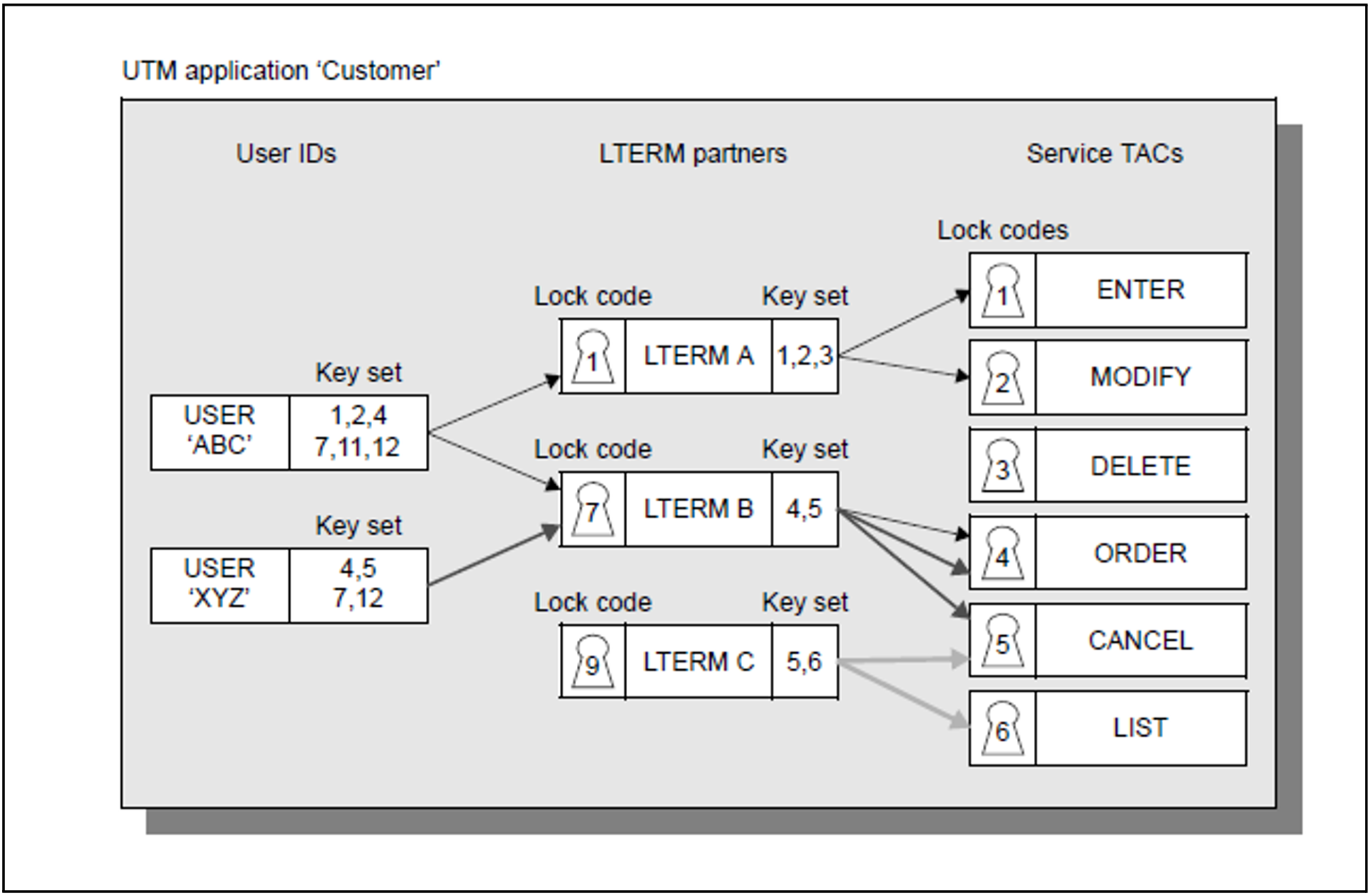
Example of how to use the lock/key code concept
Figure 33: Data access control using the lock/key code concept
A user with the user ID “ABC” wishes to work with the UTM application “Customer”. He must first identify himself to the UTM application by specifying his user ID and, if necessary, a password.
The key set of user ID “ABC” contains the key codes 1, 2, 4, 7, 11 and 12. The user can thus sign on via the client assigned to LTERM partner A (lock code 1), or via the client assigned to LTERM partner B (lock code 4). LTERM partner C is secured with lock code 9. However, since user ID “ABC” does not have the corresponding key code, any attempt to sign on via the client assigned to LTERM partner C will be rejected by the UTM application.
The user can only start a service if both his user ID and the LTERM partner have the key code that matches the lock code of the corresponding transaction code (service TAC).
LTERM partner A has the key codes 1, 2 and 3. However, since user ID “ABC” is missing key code 3, the user can only start the “ENTER” (lock code 1) and “MODIFY” (lock code 2) services via this LTERM partner.