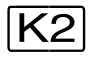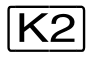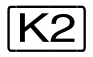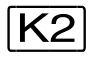User programs which process security-related data must be protected against uncontrolled input of commands. This protection must be provided in all input modes (for foreground and background procedures). To achieve this, the settings must be made within any programs which contain security-critical parts. This is also referred to as explicit program protection. It is activated by a CLISET macro call. (For further details see also chapter “Program interfaces”). This makes the programs themselves responsible for calls such as CMD, BKPT, -STXIT, etc., when security-related information is being processed.
Acceptance and rejection of events
Program | Non-interruptible | Interruptible | |
Procedure | Arbitrary | Non-interruptible | Interruptible |
key | z | r | a |
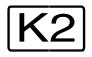
K2-STXIT | a,re | a,ri | a |
CMD macro | a,re | a,ri | a |
BKPT macro | a,re | a,ri | a |
other macros | a,re | a,ri | a |
//EXEC-SYS-CMD | r | c | a |
//HOLD-PROGRAM | r | c | c |
/HOLD-PROGRAM | r* | a* | a* |
Key:
| a: | accepted by the system |
| re: | should be rejected by the program for explicit program protection (CLISET) |
ri: | should be rejected by the program for implicit program protection (CLIGET) |
r: | rejected by the system |
c: | rejected by the system if SYSSTMT is not SYSCMD |
| a*: | regarded by the system as data if SYSSTMT or SYSDTA, as applicable, is not SYSCMD. Otherwise, it will be accepted by the system. |
| r*: | regarded by the system as data if SYSSTMT or SYSDTA, as applicable, is not SYSCMD. Otherwise, it will be rejected by the system. |
re and ri are the responsibility of the program.
Rejection of events
Interruption by is simply ignored, the processes continue running unimpaired.
/HOLD-PROGRAM, //HOLD-PROGRAM and PROGRAM-INPUT=*MIXED-WITH-CMD return EOF to the other program.
//EXECUTE-SYSTEM-COMMAND is rejected, and spin-off is activated for the statements.
//HOLD-PROGRAM is always rejected if SYSSTMT is not assigned to SYSCMD.
Coexistence of different protection modes
The two protection modes (implicit and explicit) are two different functions. They coexist, and for some events they overlap.
A protection mode cannot be inherited. Nevertheless, there are effects which are similar enough to make use of the term inheritance appropriate.
Namely:
explicit program protection includes implicit program protection,
implicit program protection includes procedure protection,
and procedure protection includes implicit program protection: however, only if this protection is provided by the program itself at the request of the procedure, by a CLIGET macro call.
Notes
Since explicit program protection is implemented by an SVC, the program can be interrupted in command mode by the key before the SVC is executed: e.g. if the key is pressed during execution of the LOAD-/START-EXECUTABLE-PROGRAM (or LOAD-/START-PROGRAM).
If pressing the key must not be allowed to interrupt an SVC in a program, it is necessary to activate a STXIT routine which intercepts the event.To avoid the SVC being terminated by test functions (e.g. AID), the program must be protected against read access. In this case, only the RESUME-PROGRAM command is allowed after the key has been pressed.
Explicit program protection can also be set in non-procedure mode (for foreground and background processes).
Implicit program protection is only relevant in procedure mode. This option cannot be set in non-procedure mode.
Where programs support implicit program protection, a number of actions which affect interruptions are prohibited - in conjunction with the procedure settings for INTERRUPT-ALLOWED. Compatible behavior must therefore be correctly provided in the programs themselves.
Implicit program protection can be activated in the procedure by a switch, by a program statement or a parameter file.
To ensure that program protection is maintained, the program should interrogate the INTERRUPT-ALLOWED setting in the procedure before each action which affects interruptions (CMD, STXIT, BKPT etc.).
A procedure can be terminated during foreground processes, whereas a program is interrupted by /HOLD-PROGRAM or //HOLD-PROGRAM. In this case, the program can restore the implicit interruption protection by continually interrogating the CLIGET interface before requesting an action which affects interruptions.
Implicit program protection against interruptions must be documented in the program specification. If it is not, any use of the program in uninterruptible procedures should be recorded.
A procedure can be protected against interruption by means of a procedure-internal program which calls BKPT in a -STXIT routine. SDF-P program functions can be used to intercept the interruption and to restart the program.
Example
/SET-PROCEDURE-OPTIONS INTERRUPT-ALLOWED=*NO
/ASSIGN-SYSOUT TO=*DUMMY "No affect on EDT for write-read"
/DECLARE-VARIABLE OPS(TYPE=*STRUCTURE),-
/MULTIPLE-ELEMENTS=*LIST
/LOAD-EXE FROM-FILE=*LIB(LIB=&(INSTALLATION-PATH( -
/LOGICAL-ID='EDT', -
/INSTALLATION-UNIT='SYSLNK', -
/VERSION=*STD, -
/DEFAULT-PATH-NAME='EDT')), -
/ELEM=EDTSTRT,TYPE=L)
/EXECUTE-CMD CMD=(SHOW-JOB-STATUS),TEXT-OUTPUT=*NONE,-
/STRUCTURE-OUTPUT=OPS,RETURNCODE=*NONE
/SHV OPS#.PROG-FILE;SHV OPS#.PROG-NAME
/WHILE (OPS#.PROG-FILE NE '')
/ RESUME-PROGRAM
/ FREE-VARIABLE OPS
/ EXECUTE-CMD CMD=(SHOW-JOB-STATUS),TEXT-OUTPUT=*NONE, -
/ STRUCTURE-OUTPUT=OPS,RETURNCODE=*NONE
/END-WHILE