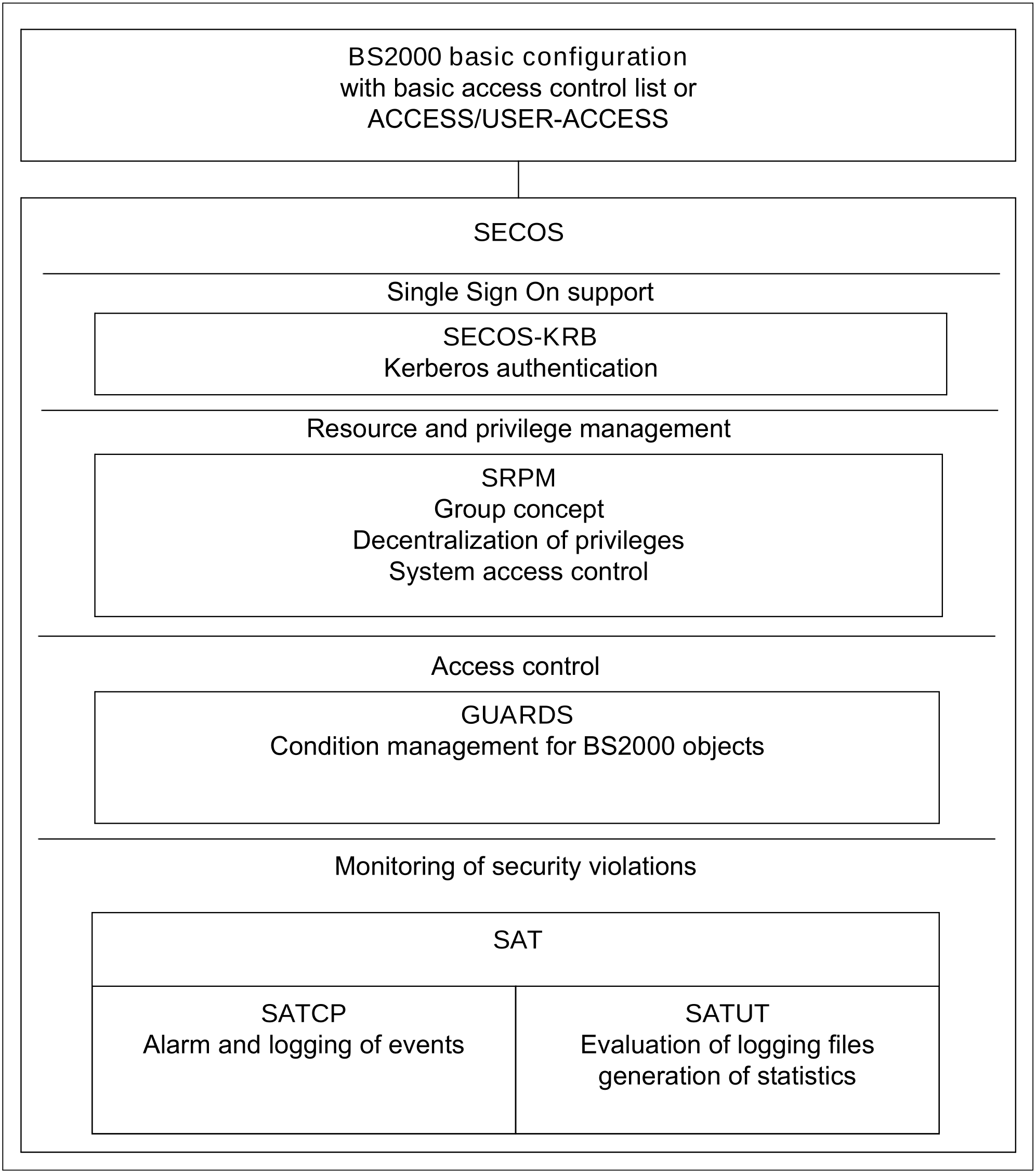
BS2000 basic configuration together with SECOS provides an operating system which is designed to meet the requirements of functionality class F2 and assurance level Q3 of the IT security criteria. The definition and the context of these security criteria are described in the “IT Security Criteria” manual [35].
Functionality class F2 is formed by the following five basic functions (simplified representation):
Identification and authentication
Users must be identified and authenticated prior to all other interactions with the operating system. For every interaction the system shall be able to establish the identity of the user.Administration of rights
The system shall be able to administer access rights between users (subjects) and objects. It shall be possible to grant the access rights down to the granularity of a single user. The administration of rights shall provide controls to limit propagation of access rights.Verification of rights
With each attempt by users to access objects that are subject to the administration of rights, the operating system shall verify the validity of the request. Unauthorized access attempts shall be rejected.Auditing
The system shall contain an audit component which is able to log events which are relevant to security. Such events are, for example, the use of the
identification/authentication mechanism, access to objects and the actions of users with special privileges.Object reuse
All storage objects returned to the system shall be treated before reuse by other subjects in such a way that no conclusions can be drawn regarding the previous contents.
From the viewpoint of the system customer, assurance level Q3 is assessed by reference to aspects of operational assurance and by its separation from components not to be evaluated (see “IT Security Criteria” manual [35]). These are the following:
The ease with which system start can be followed.
The ability to supply evidence of errors that occurred during software installation.
The reliability with which it can be ensured that ALL interventions are logged at system startup.
The separation of system components which have been evaluated from those which are not to be evaluated in order to prevent the inappropriate use, simulation and bypassing of security functions.
Significance of the security criteria for the user
If an operating system is developed and produced in accordance with F2/Q3, then this means that:
The components of the operating system have been developed in accordance with the Q3 assurance criteria and offer the basic functions of secure systems in accordance with the F2 functionality class.
This enables system administration to install and ensure operation of a trusted computing base.
The actual scope of the measures required to implement F2/Q3 is determined by the user’s security policy in accordance with the prevailing operational environment.
Figure 2: Functional units of the security package