A self-signed, system-specific certificate is preinstalled for each MU on the SE server. This is not known directly by the web browsers, nor is it derived from a known root certificate.
A standard certificate is automatically generated and activated each time the system is renamed (the FQDN is changed). The new standard certificate must then of course be accepted by or imported to the browsers.
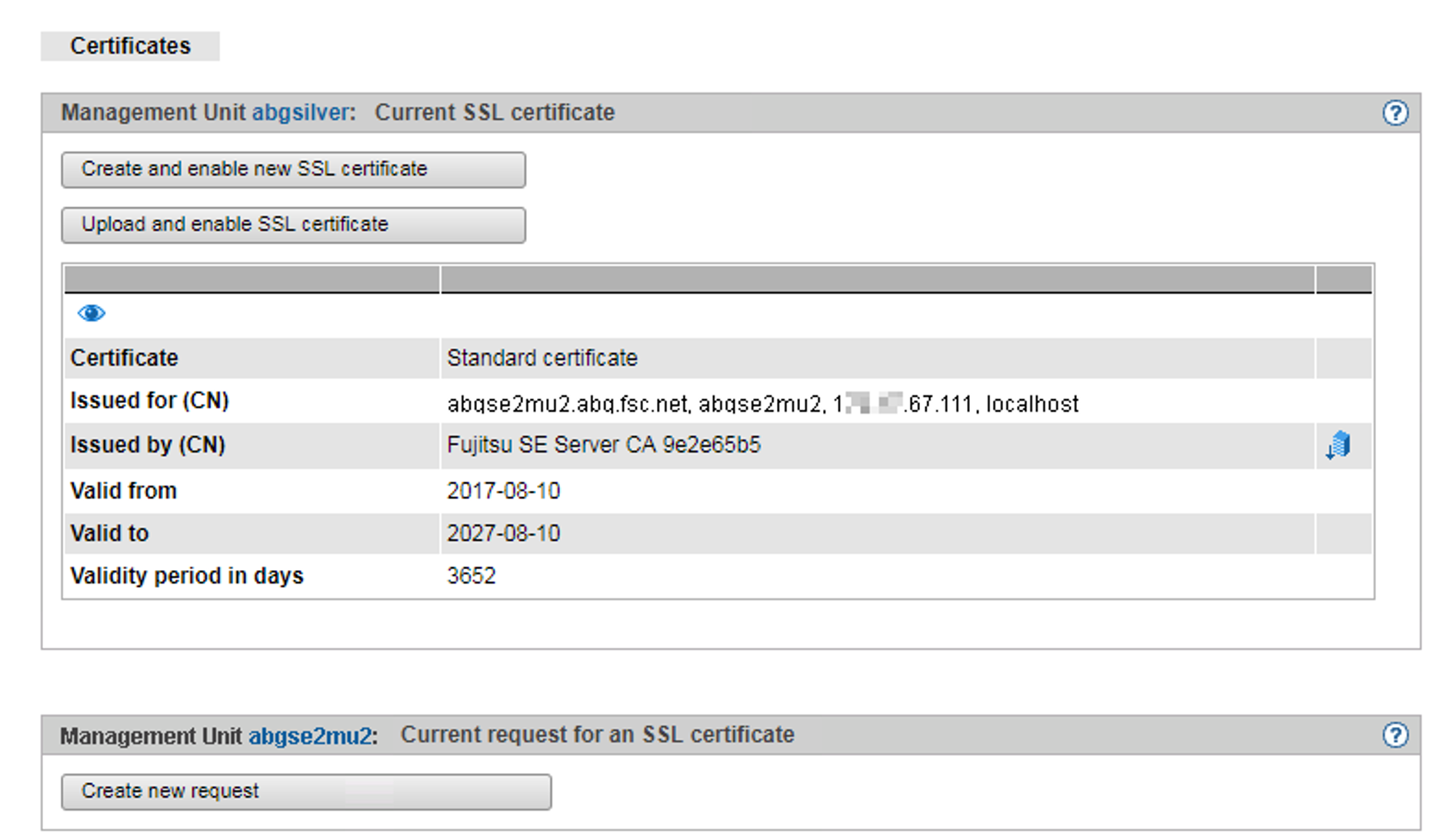
The main features of this certificate are:
The Common name (CN) is identical to the fully qualified domain name (FQDN) of the base operating system.
The validity time is 10 years.
The fingerprint which unambiguously identifies the certificate is generated using the SHA-1 algorithm and RSA encryption.
As the browser does not know the self-signed certificate, when the SE Manager is called it requests the user to accept the certificate temporarily for the current session or to import it permanently.
If you call the SE Manager on the local console, you must also confirm or import the standard certificate, because the browser used on the Gnome desktop does not know the certificate, either.
You are granted access to the SE Manager of the system only if the certificate is temporarily accepted or permanently imported.
If in doubt, you should first read and cross-check the certificate before accepting it temporarily or importing it permanently.
Displaying the current SSL certificate
> | In the tree structure select Authorizations The Certificates tab with the Current SSL certificate and Current request for an SSL certificate groups opens. The information displayed is described in the SE Manager help. |
Displaying details of the current SSL certificate
> | In the tree structure select Authorizations The Certificates tab opens. |
> | To display further details, click the Details icon () in the Current SSL certificate group. The Detailed display of the current SSL certificate dialog box opens. The information displayed is described in the SE Manager help. |