For communication at shell level, as an alternative to the terminal integrated into the SE Manager you can use the SSH client PuTTY (Version 0.63 and higher). See section "Alternative access to the BS2000 operating system with PuTTY".
The examples below refer to the SSH client PuTTY.
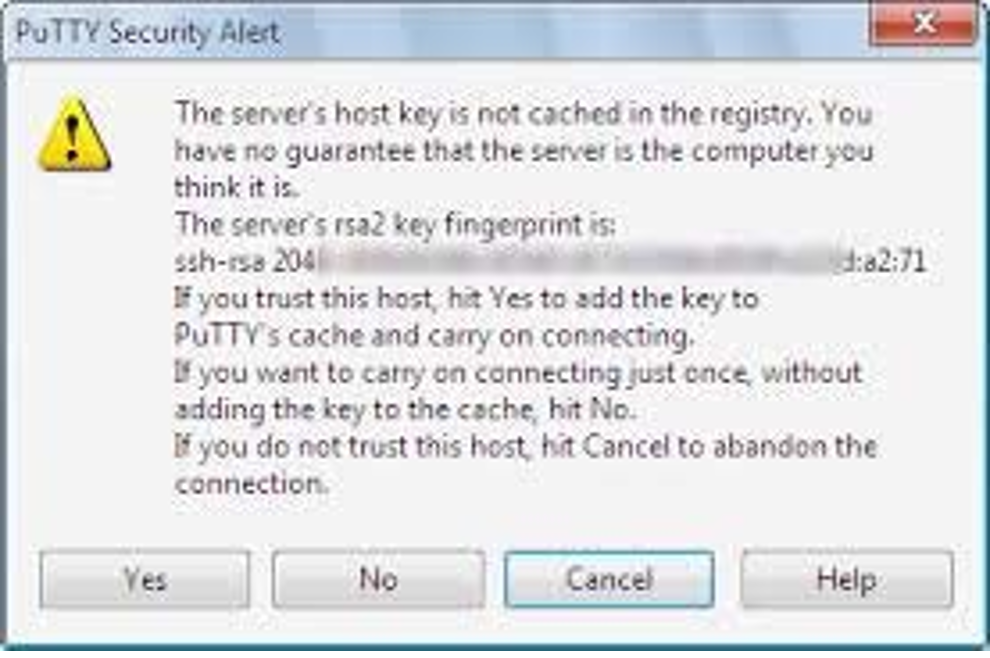
Secure Shell host key
During system installation, a host key is created on the system.
The first time a connection is set up, you must confirm this host key (depending on the SSH client) as in the following example with PuTTY.
Communication using Secure Shell keys
SSH authentication is possible not only using an account and password, but also by means of an SSH key pair.
This type of authentication should be preferred above all when programming automated procedures because a password then does not need to be coded in plain text.
Security-relevant actions
As administrator you can store SSH key (pairs).
You can provide additional protection for the stored keys by means of “passphrases”.
The key management associated with this is described in detail in the next section.