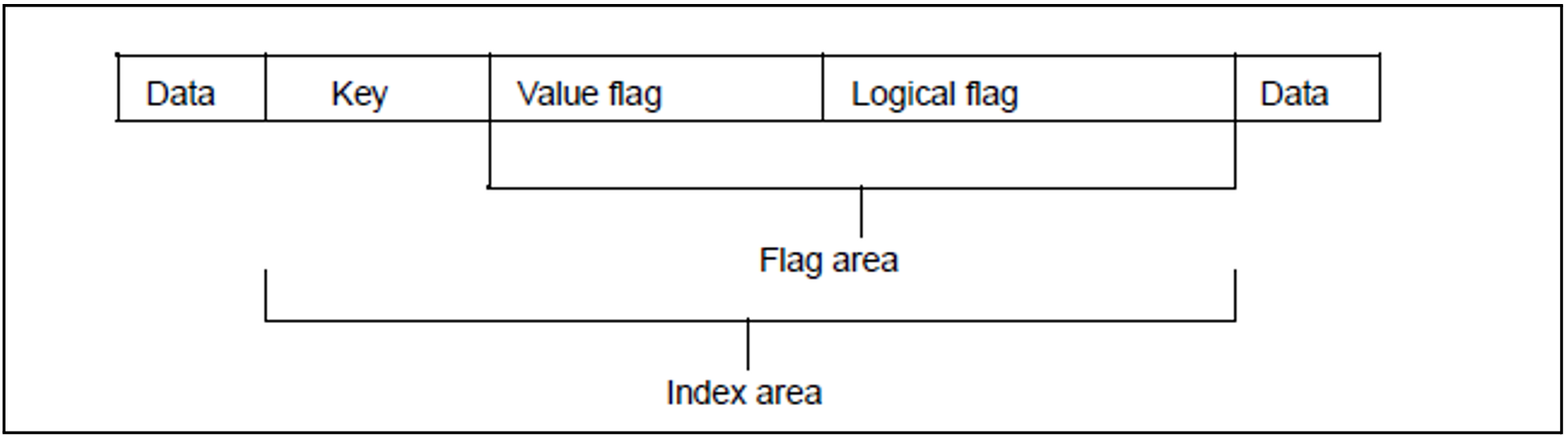
ISAM records are characterized by an index area, which is in the same position, and has the same structure, in each record of a file. The index area always contains a record key which identifies the record. In addition, the index area may contain flags which permit searching for records on the basis of certain characteristics. The total index area (key + flags) may not exceed 255 bytes in length.
ISAM keys
Each record in an ISAM file must have a key with a length of at least one byte. The position of this ISAM key in the record is defined for all records of the file in FILE/FCB (operand KEYPOS) or in the ADD-FILE-LINK command (operand KEY-POSITION). The user must take the record format (see "ISAM record formats" (Record with secondary keys (NK-ISAM))) into account when defining the key position. In files with variable-length records, for example, the ISAM key cannot begin before position 5 (KEYPOS >= 5) because 4 bytes are needed for the record length field and for control information.
The length of the ISAM key is defined via the KEYLEN operand in FILE/FCB or via the KEY-LENGTH operand in ADD-FILE-LINK. When defining the key length, the user must remember that the maximum index length must not exceed 255 bytes (key + flags).
In K-ISAM, the key length may affect the file size and processing performance. Since the complete key is placed in the index block, the key length will determine how many index entries will fit into one index block.
With NK-ISAM, DMS uses key compression to optimize the number of index entries in each index block, so that longer keys are, on average, compressed to a length of 3-5 bytes and each index block can hold, on average, 160 entries. The number of index entries in an index block affects, in turn, the total number of index blocks needed, and thus the number of index levels in the file and the performance when accessing a record.
Duplicate ISAM keys
The principle of ISAM file processing is based on unique keys. If DUPEKY=YES is specified in FILE/FCB or if DUPLICATE-KEY is specified in the ADD-FILE-LINK command, the user can create files which may contain duplicate keys.
During write operations a record with a key which already exists in the file is always written after the last existing record with the same key. The records with identical keys are thus stored in the file in the chronological order in which they were written.
NK-ISAM adds a time stamp to records with keys which already exist in the file. Via the time stamp the records can be kept in the correct order, i.e. corresponding to the time at which they were written.
Sequential read operations always return the records in the order in which they were written. For “reverse” reading, the records are returned in the opposite sequence.
Non-sequential reading with the record key always returns the first record of a group of records with the same keys. The remaining records of the group must then be read sequentially.
If, during shared-update processing of NK-ISAM files, a record lock is set, then this lock affects all records with the same key.
Flags in the ISAM index
In addition to the ISAM key, value flags or logical flags can be used to search for records. These flags follow the key in the ISAM index area of each record, the value flags preceding the logical flags if both types are used. In NK-ISAM, the flags are not included in the index entry, but are evaluated sequentially within NK-ISAM. For the user, this means that there will be a performance drop if flagged records are used, but processing of such records is otherwise the same as in K-ISAM.
Flag processing in NK-ISAM is considerably less efficient than in K-ISAM.
In K-ISAM, the flags are included in the index entries and are propagated as a component of the ISAM index – through all index levels of the file. However, inclusion of the flags in the index entry is carried out differently for value and logical flags.
The position of the value flag is determined by the position and length of the preceding key (KEYPOS + KEYLEN) and its length is defined by means of VALLEN in the FILE and FCB macros or with the VALUE-FLAG-LENGTH operand in the ADD-FILE command. For the logical flag, the position is determined by the sum of the key position, the key length and
the length of the value flag. The length is determined by the LOGLEN operand in the FILE and FCB macros or by the LOGICAL-FLAG-LENGTH operand in the ADD-FILE-LINK command.
When searching for a record with the aid of a value or logical flag, the contents of the flag area of the records being checked are compared with the specified value or with a logical bit mask. DMS returns the first record which fulfills the search condition.
In the case of K-ISAM, the value information of the index entries is created on the basis of what the user specifies for VALPROP in the FILE and FCB macros or for PROPAGATE-VALUE-FLAG in the ADD-FILE-LINK command. If the function MAX (MIN) is specified, each index entry contains the maximum (minimum) value flag in the block of the next lower level (data or index block) to which it points. Whether the propagation of the maximum or minimum value flag serves any purpose depends on how the records are subsequently to be retrieved. The usefulness of a value flag increases the more evenly the value flags rise or fall as the ISAM key ascends.
In the logical flags, binary attributes of the object described by the record can be encoded in individual bits. All logical flags of a data (or index) block are ORed together and passed on to the (next-higher) index entry. When searching for records with certain attributes, DMS can decide, immediately after checking the index entry, whether or not the block that this entry points to contains records with these attributes.
If the value for VALLEN (or VALUE-FLAG-LENGTH) or LOGLEN (or LOGICAL-FLAG-LENGTH) is not zero, DMS assumes that this is a flagged file. If the file already exists (i.e. the OPEN type is INPUT, INOUT or EXTEND), the catalog values for VALPROP (or PROPAGATE-VALUE-FLAG) and/or VALLEN (or VALUE-FLAG-LENGTH) are used. LOGLEN (or LOGICAL-FLAG-LENGTH) must always be specified if the file was created with a flag area. The catalog values cannot be modified by means of a FILE or FCB macro or ADD-FILE-LINK command.
Example: value flags
Let us assume that the “year of birth” is to be used as the value flag in a personnel file and that VALPROP=MIN was specified in the catalog entry. This would mean that the lowest birth year of the personnel records contained in each block would be transferred to the index block.
Suitable query: which staff members were born before 1950 ? – Thanks to the value flag, entire blocks can be immediately skipped when searching.
Unsuitable query: which staff members were born after 1950 ? – In this case, all records of a block must be checked. A file with VALPROP=MAX would be more appropriate here.
ISAM record formats
ISAM files may have fixed-length or variable-length records, i.e. records with format F or V. This format is specified in the RECFORM operand of the FCB and FILE macros or with the RECORD-FORMAT operand of the ADD-FILE-LINK command.
If RECFORM=V is specified, the user must remember, when defining the key position and the maximum record length, that the data is preceded by a 4-byte field. For fixed-length records (RECFORM=F), the user does not need to worry about this 4-byte field when defining the key position, although ISAM still. internally, places a 4-byte field in front of each record.
The table below indicates the effects of the record format on the record length defined by means of a macro or command.
Operand in | Operand in | Meaning of RECSIZE or RECORD-SIZE |
|---|---|---|
RECFORM=F | RECORD-FORMAT= *FIXED | Specifies, in bytes, the length valid for all records |
RECFORM=V | RECORD-FORMAT= *VARIABLE | Specifies the maximum length of a record; RECSIZE=BLKSIZE or RECORD-SIZE= BUFFER-LENGTH, as appropriate, are then used as default values |
If RECSIZE approaches BLKSIZE (implicitly or explicitly), overflow blocks may be created in NK-ISAM (see section "Overflow block (NK-ISAM)") and this may lead to an increase in the number of I/O operations.
If, for access to an existing file, the value specified for RECSIZE or RECORD-SIZE is too small, this may affect read operations: if DMS reads a longer record, it returns only the number of bytes specified in RECSIZE to the receive field defined by the use and then aborts the read operation with an error message. The user can intercept this with a suitable error routine in his/her program.