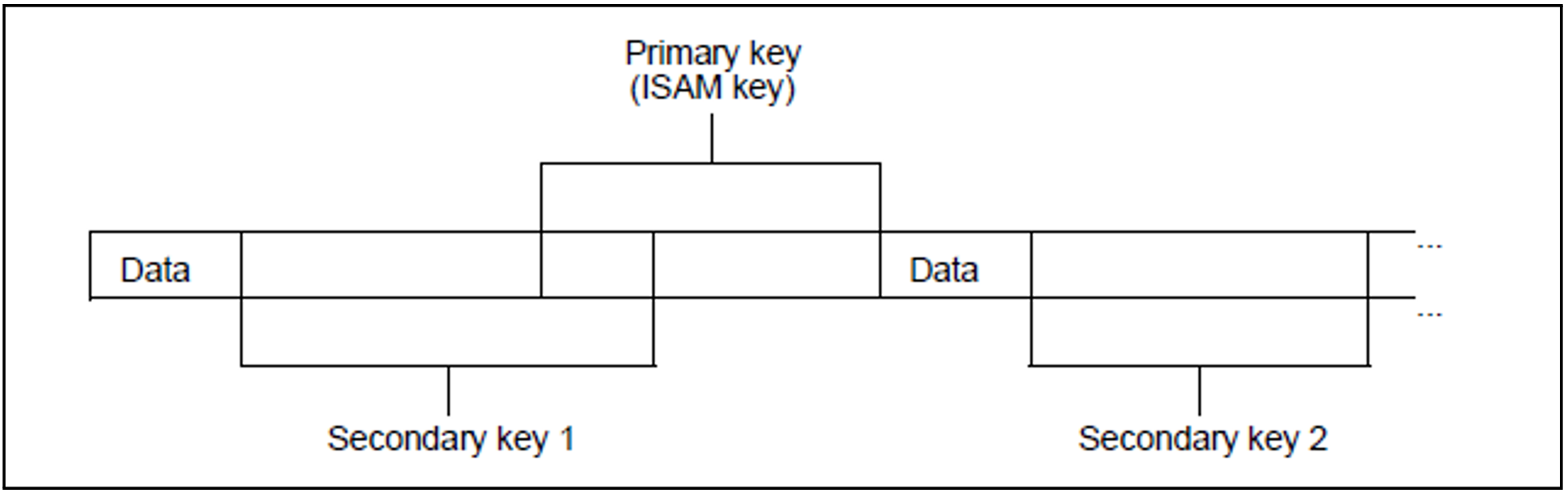
In addition to the ISAM key (primary key), the records of NK-ISAM files may contain up to 30 secondary keys via which the user can locate the desired records.
In contrast to conventional ISAM files, a file with secondary keys may contain neither value flags nor logical flags. However, the secondary keys mean that these extra features of the ISAM key are no longer required in any case. The length of the primary key must not exceed 255 bytes. The length of each secondary key must not exceed 127 bytes.
The secondary keys may overlap each other and may overlap the primary key. A record with secondary keys could, therefore, have the following structure:
Primary key (ISAM key)
Each record in an ISAM file must have a primary key with a length of at least one byte. The position of the primary key within the record is defined for all records of the file with the KEYPOS operand of the FILE and FCB macros or via the KEY-POSITION operand of the ADD-FILE-LINK command. The user must take the record format (see "ISAM recordformats") into account when defining the key position. In files with variablelength records, for example, the ISAM key must not start before position 5 (KEYPOS >= 5 or KEY-POSITION >= 5), since the first four bytes of each record are used for the record length field and control information.
The key length is defined via the KEYLEN operand in the FILE/FCB macro or via the KEY-LENGTH operand in the ADD-FILE-LINK command. The maximum permissible key length is 255 bytes. Logical flags and value flags are not permitted.
By means of key compression, DMS optimizes the number of index entries in each index block, so that longer keys are, on average, compressed to a length of 3-5 bytes and each index block can hold, on average, about 160 entries.
The number of index entries in an index block affects, in turn, the total number of index blocks needed, and thus the number of index levels in a file and the performance when accessing a record.
Secondary keys
In addition to the primary key, a record may contain up to 30 secondary keys. Just like the primary key, each secondary key has the same length and the same position in each record of the file.
In contrast to the primary key, the attributes of a secondary key (position, length, whether duplicate keys are permitted) are not kept in the catalog entry for the file, but in its control block. For this reason, they cannot be displayed by means of the FSTAT macro or the SHOW-FILE-ATTRIBUTES command. In order to enable the user to obtain information on the secondary keys of a file, ISAM therefore now provides the SHOWAIX macro and the SHOW-INDEX-ATTRIBUTES command.
A further difference between the primary key and a secondary key is that the secondary key is identified by a name. This is necessary because there may be several secondary keys defined for one file (whereas there is only ever one primary key).
Secondary keys can be defined only for an existing file, i.e. for a file which has been opened at least once with OUTPUT or OUTIN. The file may be empty, but users are advised, for reasons of performance, not to set up secondary keys for a new file until it has been filled with records.
The user can define a secondary key for a file via the CREAIX macro or the CREATE-ALTERNATE-INDEX command.
The position of the secondary key is specified via the KEYPOS operand of the macro or the KEY-POSITION operand of the command. Just as for the primary key, the 4 bytes for the record length field and control information must be taken into account in the case of files with variable-length records (see "Primary key (ISAM key)").
The length of the secondary key is specified via the KEYLEN operand of the macro or the KEY-LENGTH operand of the command. A secondary key may be up to 127 bytes long. Both the number of secondary keys and their lengths affect the file size and the performance: since the entire secondary key is placed (without compression) in the secondary index block, the key length determines how many index entries will fit into one secondary index block.
The KEYNAME operand of the macro and the KEY-NAME operand of the command assign a name to the secondary key. The user can then specify this name in the macros GET, GETR, GETKY and SETL to refer to the secondary key to be used (in a manner similar to that for the primary key) for read and pointer operations. This name can also be specified in the DELAIX macro or the DELETE-ALTERNATE-INDEX command to identify a secondary key which is to be deleted. The user can obtain information about all secondary keys defined for a file with the aid of the SHOWAIX macro or the SHOW-INDEX-ATTRI-BUTES command.
Duplicate secondary keys
In files with secondary keys, the values of the primary key must be unique. In contrast, there may be duplicate secondary keys unless the user precludes this by specifying
DUPEKY=NO in the CREAIX macro or DUPLICATE-KEY=*NO in the CREATE-ALTERNATE-INDEX command.
Internally, DMS creates one or more secondary index blocks for each secondary key defined for a file. In this index, it creates an entry for each value of this secondary key which occurs in the file. This entry points to the primary key of the corresponding record. (For further details, see "Secondary index block (NK-ISAM)" (Primary index block (ISAM index block) and secondary index block)). If a given secondary key value occurs in several records, then the associated entry in the secondary index block also contains several pointers to the primary key values of these records. These pointers are stored in the order in which they are created, i.e. in the order in which they were written to or modified in the secondary index block. (For reasons of internal management, DMS appends a time stamp to each such pointer to a primary key when it is created.)
Sequential read operations via a secondary key thus return the records in the order in which the pointers to the associated primary key values were created, i.e. in the order in which they were written to or modified in the secondary index block. For “reverse read” operations, the records are returned in the reverse of this order.
Non-sequential read operations via a secondary key always return the first record of the group with identical secondary key values. The remaining records of the group must then be read sequentially.
Flags in the ISAM index
Neither value flags not logical flags are permitted in files with secondary keys.
ISAM record formats
With respect to record formats, the notes outlined for records without secondary keys (see "Record without a secondary key") also apply to records with secondary keys.
If secondary keys are subsequently defined for a non-empty file with RECFORM=V or RECORD-FORMAT=*VARIABLE, it must be remembered, when specifying the key position and key length, that the shortest record in the file must contain the entire secondary key being defined.