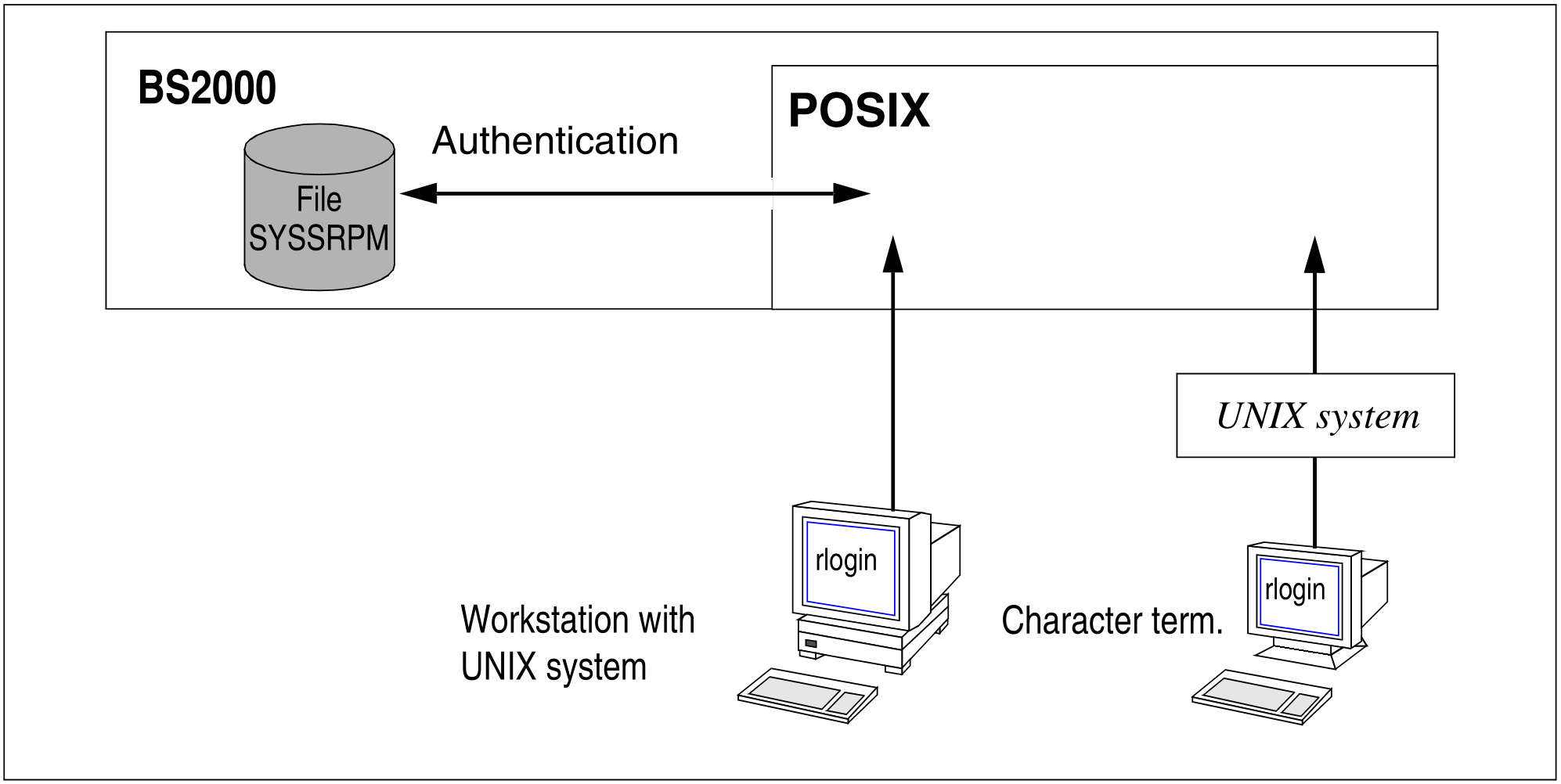
POSIX can also be used from remote computers (see section “Accessing the POSIX shell”). Users who signed on to POSIX using the rlogin command are entered as local users in the BS2000 user administration of the central computer. The BS2000 module SRPM checks the access rights during rlogin processing.
Figure 15: Access protection for access via rlogin
The following applies for the rcp and rsh commands:
Access rights are handled as in UNIX, i.e. authorized hosts and users are taken from the $HOME/.rhosts file. For SECOS, this can also be set using BS2000 systems, see section “Defining access rights for users of remote computers”.
ATTENTION!
Entries in the /.rhosts file (in the Root directory) enable commands to be executed under TSOS and are thus relevant to security!